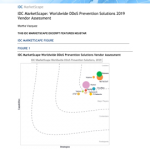
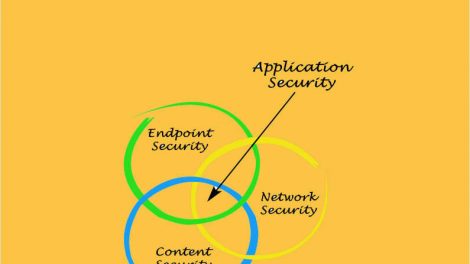
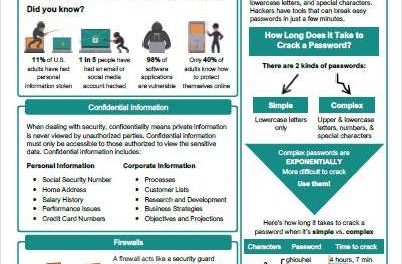
Find out what to look for in an endpoint security solution. Use this expert list of requirements and features to evaluate and select the best...
Author - adminb2b
Businesses worldwide are at risk for security breaches. While large, well-known companies seem like a likely target, small and medium-sized...
Detect Fraud, Manage Risk, and Increase Revenue Streams with SearchUnify. Read this datasheet to find! Leading insurance companies are submerged with...
Security must cover every single endpoint device through the entire lifecycle Nearly every device will work through the cloud in some way, and 80% of...
In this eBook, learn how Voice AI in the contact center can help you beat the benchmarks, with new ideas and techniques to enhance your quality...
Security operations (SecOps) leaders say they struggle to detect hidden and unknown threats with legacy tools, mitigating the potential threats of...
With weaponized AI on the horizon, cyber-attacks will become more sophisticated and evasive than ever before. Supercharged phishing emails and self...
As more organizations are shifting infrastructure and services to the cloud, more are adopting a multicloud strategy. But for all the benefits of a...
Cloud security is a journey, not a destination. The guidance offered by the NSA is a critical step in raising awareness and provides insight, so...
The World Health Organization officially declared COVID-19 a pandemic. While companies around the world take proper precautions to protect their...