4 key trends from spear phishing to credentials theft. Email threats cost organizations an estimated $1.77 billion in losses last year – and...
Author - adminb2b
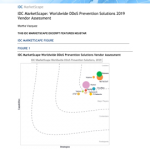
This white paper evaluates the development of known OT attack campaigns, and the wider progression of malware, in order to identify trends and...
This report details seven case studies of attacks that were intercepted and neutralized by cyber defense AI, including insider threat, ransomware...
This document features case studies of alerts raised in real industrial networks where Darktrace Industrial was deployed. Powered by unsupervised...
With the rise in industrial IoT and convergence between Operational Technology and IT, industrial control systems are increasingly vulnerable to...
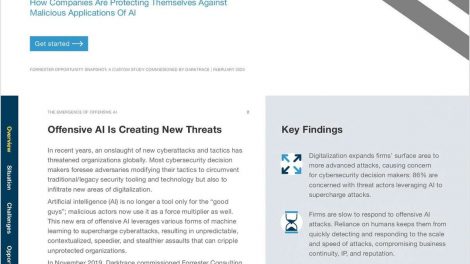
Learn how companies are protecting themselves against malicious applications of AI. Malicious actors are now beginning to leverage AI as a force...
TekStream and Splunk have joined forces to help DoD contractors get on the fast track to CMMC compliance. CMMC is new and confusing, but TekStream...
Digital payments have become ubiquitous as consumers use credit, debit, and mobile payments to buy groceries and clothing and even repay friends. Yet...
Learn how to improve decision making. As artificial intelligence, machine learning, and data science are fundamentally changing the world, we need to...
Allstacks’ Measure What Matters Demo Series Join us as we demonstrate real-world scenarios of how to use Allstacks’ insights and reports to...