In order to take full advantage of modernization while still meeting the high public-sector expectation around security, government needs a new...
Author - adminb2b
When you need information to make strategic decisions Planet Federal gives you access to the largest satellite imaging constellation in orbit...
With security a critical concern across a wide spectrum of industries, ensuring security on embedded devices has become a key element of an...
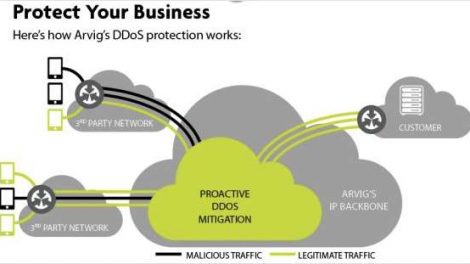
DDoS Attacks Remain A Threat to Businesses Hackers use Distributed Denial of Service (DDoS) attacks to take business websites offline with floods of...
When Security and Choice Matter Access hardware delivers security, controlled access, and productive operation to your machine building designs...
The proliferation of remote work has created, and will continue to create, risks for trade secret protection with long-term consequences. Companies...
Remote work and the move toward more workflow automation could be sticking around as firms continue to cut overhead and bolster efficiency in an...
The longer regulators wait, the more widely used algorithmic decision-making systems become. In the process, the concrete harms these technologies...
Free cybersecurity “how to” guide and 3 tools to help accelerate data protection across people, processes, people, and technology There...
With more and more organizations responding to growing COVID-19 disruptions by allowing employees and students to work from home via the internet...